.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

For many years, SMBs and mid-market businesses in GCC & Africa have believed one simple thing: “If I have antivirus installed on my computers, my business is safe.”
It feels logical. Antivirus is affordable, widely marketed, and almost every new laptop comes preloaded with some form of it. For decades, it was indeed the first line of defense.
But here’s the truth: in today’s world of ransomware, fileless attacks, phishing, zero-day exploits, and supply-chain compromises, antivirus alone is like locking your front door while leaving all your windows open.
Cybercriminals don’t stop where antivirus stops. They innovate daily. And unfortunately, SMBs and mid-market firms — already stretched thin with IT resources — are their favorite targets.
This blog will explain in detail why traditional antivirus is no longer enough, share real-world stories of SMB breaches, explain how modern Endpoint Detection & Response (EDR) with Zero Dwell Containment changes the game, and finally, show how FSD-Tech’s MSSP model makes this advanced protection affordable and manageable for businesses like yours. To Keep this simple, we have divided this blog into 6 parts.
Don’t Wait for a Breach to Expose Your Business. Get a Free Cybersecurity Assessment Today.
1.1 The Old World of Malware
In the 1990s and early 2000s, threats were mostly viruses — malicious programs that could be detected with a simple signature. Antivirus worked well because:
Think of it like police having a “Most Wanted List”. If the criminal’s face was on the list, they could be caught.
1.2 The New World of Advanced Threats
Fast forward to today. The cyber landscape has transformed:
Reality Check: A 2025 AV-TEST report noted over 450,000 new malware variants are created daily. No antivirus vendor can update fast enough.
1.3 Why SMBs and Mid-Market Firms Are Easy Targets
Large enterprises have full SOC (Security Operations Center) teams, threat hunters, and millions in budget. SMBs don’t.
SMBs often:
Attackers know this. Which is why 43% of cyberattacks target SMBs, and 60% of SMBs shut down within 6 months of a major cyber incident.
2.1 Detection Delay = Breach
Antivirus waits until a file matches a known “bad” signature. But new threats don’t have signatures yet.
Example: A Dubai-based logistics company was hit by ransomware disguised as a PDF invoice. Antivirus didn’t recognize it. Within hours, their shipment schedules were encrypted. Downtime cost them $250K in penalties.
2.2 Fileless Attacks Go Unnoticed
Antivirus looks for files. But modern attacks use PowerShell, macros, and memory execution.
Example: A small accounting firm in Nairobi was hacked via a phishing email. No malware file — the attacker used a built-in Windows tool. Antivirus didn’t detect it. The firm lost confidential client data, resulting in lost contracts.
2.3 Insider Threats Bypass Antivirus
If an employee downloads a malicious attachment intentionally or unknowingly, antivirus may not flag it.
Example: A mid-sized retail chain in Riyadh lost POS (Point-of-Sale) data because an insider installed a “free app.” Antivirus ignored it. The result: stolen credit card details of 5,000 customers.
2.4 Antivirus Does Not Monitor Behavior
Cyberattacks today are not just “bad files.” They are a series of suspicious behaviors (like privilege escalation, lateral movement, data exfiltration). Antivirus doesn’t connect the dots.
Conclusion of Part 2: Antivirus is reactive, limited, and blind to new methods. Businesses relying on it alone face massive financial, reputational, and operational risks.
Your antivirus won’t stop tomorrow’s threats. Secure a FREE Cyber Risk Health Check for your business. Sign up today.
3.1 What is EDR?
Endpoint Detection & Response (EDR) goes beyond antivirus:
3.2 What is Zero Dwell Containment (Xcitium Advantage)?
Xcitium’s Zero Dwell Containment is a game-changer:
Think of it as: “Every visitor enters a glass quarantine room until they’re proven safe. They can’t touch the rest of the building.”
3.3 Why This Matters for SMBs
AV Labs named Xcitium the 2025 Product of the Year for Advanced In-the-Wild Malware Protection.
4.1 The IT Resource Gap
Even if you had the best EDR, who will monitor it 24/7? Who will respond at 2 AM when a ransomware attempt occurs?
SMBs can’t afford a full SOC team. Hiring threat hunters is expensive.
4.2 MSSP = Enterprise Security at SMB Cost
FSD-Tech as your Managed Security Service Provider (MSSP) solves this:
4.3 MSP + MSSP Advantage
FSD-Tech isn’t just MSSP — we’re also an MSP (Managed Service Provider). That means:
4.4 Affordability for SMBs
If You’re a CEO:
Think beyond “cheap antivirus.” Think business continuity, reputation, and customer trust.
If You’re a CFO:
Calculate the cost of a single breach vs predictable MSSP subscription.
If You’re a COO:
Understand downtime = lost contracts, missed SLAs, angry customers.
If You’re an IT Manager:
Relieve alert fatigue. Gain 24/7 SOC support without extra hires.
Cybercriminals have evolved. SMB defenses must evolve too.
Antivirus alone is like bringing a shield to a gunfight.
With Xcitium EDR + Zero Dwell Containment powered by FSD-Tech MSSP, you can finally:
We don’t just sell you EDR — we manage it for you. With FSD-Tech’s Managed EDR Service:
This means you focus on running your business, while we focus on keeping it safe.
Antivirus is reactive. It waits until it’s certain something is a threat — and by then, it may be too late.
EDR with Zero Dwell is proactive. It acts immediately, stopping even unknown threats before they can harm your business.
In today’s high-speed threat landscape, this isn’t just an upgrade — it’s essential survival gear for your business.
Upgrade your security from “basic” to “bulletproof.”
Talk to FSD-Tech today about Xcitium EDR with Zero Dwell Containment, managed 24/7 by our SOC experts. Schedule Demo now
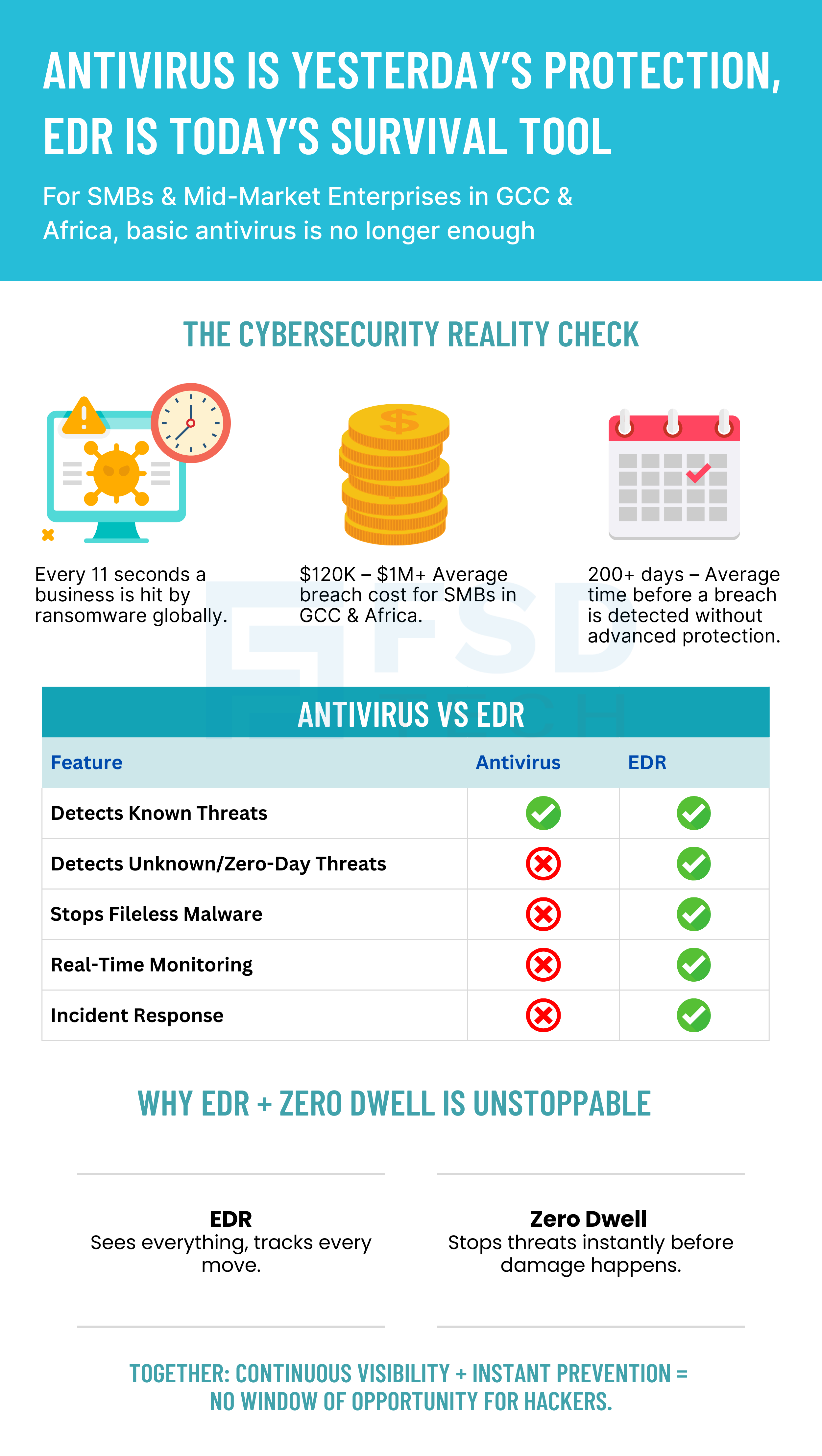
Traditional antivirus only blocks known threats using “signatures.” But today’s attackers use fileless attacks, zero-day exploits, and ransomware that antivirus doesn’t recognize. It’s like locking your front door while thieves enter through a window.
Antivirus = looks for “bad files.”
EDR (Endpoint Detection & Response) = monitors all activities (files, memory, user actions). It detects suspicious behavior, not just malware. This makes it far more effective for SMB cybersecurity.
It means unknown files are trapped instantly in a safe container before they can harm your system. Imagine every stranger entering your office is placed in a glass room until proven safe. That’s what Xcitium does with files.
Hackers create new malware every day that antivirus doesn’t recognize. They also use tools already built into Windows (like PowerShell), which antivirus ignores. That’s why ransomware often slips past antivirus.
Yes. In fact, SMBs are prime targets because:
You risk:
In GCC, downtime can cost thousands per hour (missed contracts, SLA penalties). In Africa, lost data may mean lost customers permanently. Recovery often costs 10x more than MSSP protection.
No. With FSD-Tech MSSP, you don’t need in-house expertise. Our SOC team monitors your endpoints 24/7, investigates threats, and responds instantly. You just get reports and peace of mind.
We offer predictable, monthly subscription pricing. You pay per endpoint or per user, not huge upfront costs. It’s far cheaper than hiring even one cybersecurity expert internally.
No. Unlike older “sandboxing” solutions, Xcitium lets employees keep working while unknown files are analyzed in the background. Productivity is not interrupted.
Yes. If an employee clicks a malicious link or downloads a fake invoice, EDR detects abnormal activity. Zero Dwell Containment traps suspicious files instantly, so phishing can’t escalate into ransomware.
FSD-Tech MSSP with Xcitium provides compliance-ready reports. You get audit logs, incident reports, and endpoint visibility that prove you’re meeting data protection laws.
If an employee installs unauthorized software or tries to move sensitive data, EDR detects the unusual behavior and alerts the SOC. Antivirus would never notice.
No. In fact, SMBs benefit most from MSSPs. Instead of hiring a full security team (expensive), you outsource to FSD-Tech MSSP for a fraction of the cost but get enterprise-grade protection.
MSSP (Managed Security Service Provider): Manages your security (EDR, monitoring, threat response).
With FSD-Tech, you get both in one — IT + Security.
Alert fatigue happens when IT staff receive thousands of meaningless alerts daily. They get overwhelmed and miss real threats. FSD-Tech MSSP filters alerts, investigates them, and only escalates true incidents.
Yes. The moment ransomware tries to execute, it is contained in a safe environment. It cannot touch real files or spread in your network. Unlike antivirus, it doesn’t “wait to recognize” the ransomware.
Simple:

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts