.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

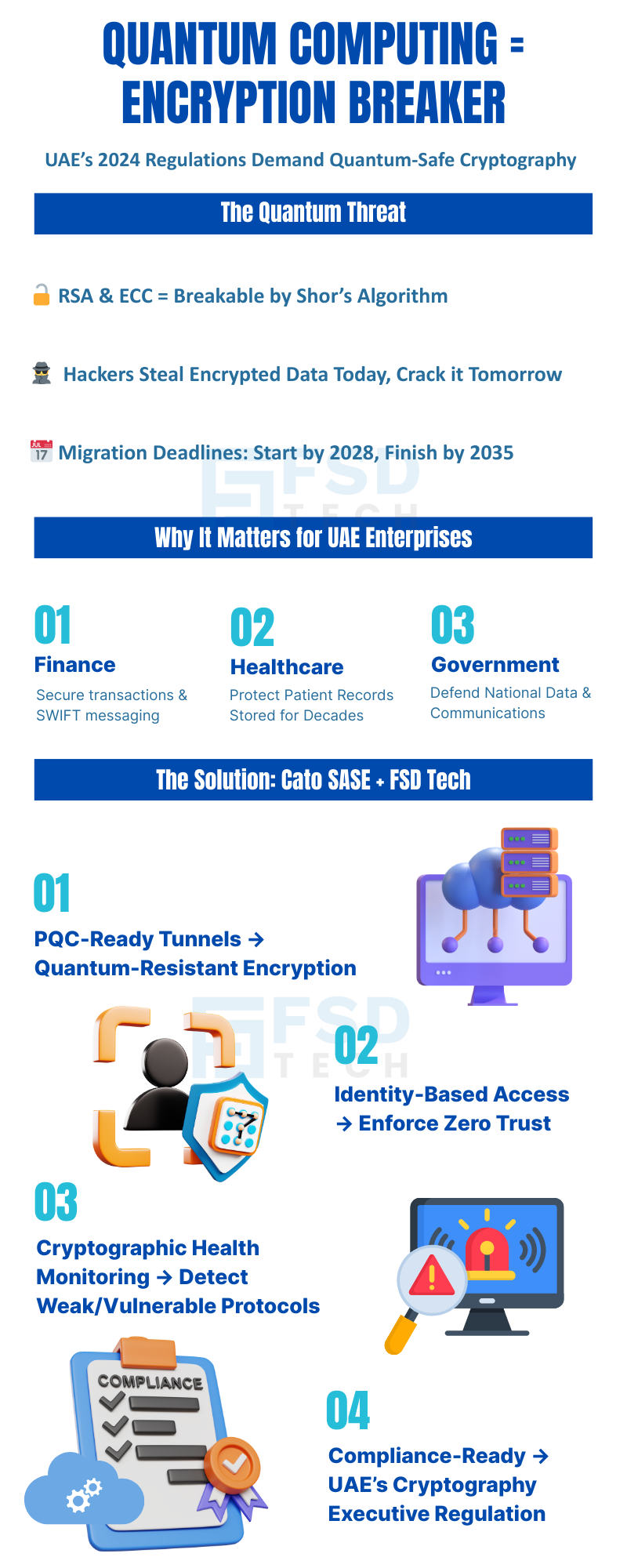
Quantum computing is rapidly transitioning from theoretical research to practical reality. As global investment accelerates, quantum computers are poised to disrupt the very foundation of digital security—public-key cryptography. Algorithms like Shor’s will soon render RSA and ECC, the backbone of today’s secure communications, obsolete. For CISOs, IT architects, and compliance leaders in the UAE and GCC, this is not a distant concern but an urgent call to action.
The UAE has positioned itself as a global leader in quantum cyber preparedness. With the 2024 Cryptography Executive Regulation, quantum-resistant cryptography is now mandatory for government and critical sectors including finance, healthcare, and utilities. This regulatory foresight, combined with the region’s rapid digital transformation, places quantum resilience at the core of national security and economic competitiveness.
Classical encryption schemes like RSA and ECC depend on the computational difficulty of factoring large numbers or solving discrete logarithm problems—tasks that would take classical computers millions of years. Quantum computers, leveraging superposition and entanglement, can solve these problems exponentially faster. Shor’s algorithm, in particular, can break RSA and ECC, exposing all data protected by these schemes to compromise.
The quantum threat is not confined to the future. Adversaries are already collecting encrypted data with the intent to decrypt it once quantum computers become available—a tactic known as “harvest now, decrypt later.” This places any sensitive or long-lived data at risk, including financial transactions, healthcare records, and government communications. Once quantum computers reach sufficient scale, previously collected data can be instantly compromised.
While the precise moment of “Q-Day”—when quantum computers can break today’s encryption—is debated, consensus among global and regional regulators is clear: organizations must begin migrating to quantum-safe cryptography now. International bodies recommend starting by 2028 and completing critical migrations by 2035. The UAE’s regulatory environment accelerates this timeline, especially for organizations in regulated sectors.
Take the first step toward quantum resilience today — don’t wait for Q-Day. Click Here
Recognizing the existential threat posed by quantum computing, NIST has led the global standardization of post-quantum cryptography. Kyber (for encryption) and Dilithium (for digital signatures) are among the first algorithms selected for standardization, offering robust defenses against both classical and quantum attacks. These algorithms are engineered to protect data for decades, ensuring long-term confidentiality and integrity.
The UAE’s Cryptography Executive Regulation, effective since 2024, mandates the adoption of quantum-resistant cryptography for all government entities and critical infrastructure operators. Compliance is enforced through regular audits and technical assessments. Non-compliance exposes organizations to regulatory penalties and, more critically, to the risk of catastrophic data breaches once quantum computers are operational.
Global cybersecurity authorities urge organizations to initiate PQC migration planning by 2028 and finalize upgrades by 2035. In the UAE, these deadlines are even more aggressive for critical sectors. CISOs must act now to inventory cryptographic assets, assess vulnerabilities, and develop a phased migration plan aligned with both regulatory requirements and operational realities.
Banks and financial institutions are high-value targets for quantum-enabled attacks. The confidentiality of transactions, interbank communications, and customer data depends on strong encryption. A quantum breach could erode trust in the financial system and trigger regulatory and reputational crises. Frameworks like STL-QCRYPTO recommend sector-specific migration plans, prioritizing payment systems, SWIFT messaging, and customer authentication.
Real-World Scenario:
A leading UAE bank, facing regulatory deadlines, engaged FSD Tech to inventory all cryptographic assets. Legacy VPNs using RSA were identified as critical risks. Migrating to PQC-ready tunnels on Cato SASE ensured compliance and future-proofed customer data against quantum threats.
Healthcare providers and utilities are responsible for sensitive data and critical operational systems that must remain secure for decades. Patient records, operational data, and control systems are all susceptible to “harvest now, decrypt later” attacks. The UAE’s regulations mandate quantum-safe upgrades, with compliance audits ensuring that all cryptographic protocols are up to date.
Example:
A Dubai hospital, storing patient records for decades, adopted Cato SASE and PQC solutions to secure its data. This not only met regulatory requirements but also protected patient privacy and operational continuity.
Government agencies manage sensitive national data, from citizen records to defense communications. The UAE’s proactive regulatory approach ensures that all government entities transition to quantum-safe cryptography, setting a benchmark for global best practices and national resilience.
Secure your sector’s future — align with UAE’s quantum-safe regulations now. Click Here
Secure Access Service Edge (SASE) is a transformative architecture that converges networking and security functions into a unified, cloud-native platform. For organizations navigating the complexity of PQC migration, SASE offers a scalable, manageable, and future-proof solution.
Cato’s SASE platform, delivered by FSD Tech in the UAE and GCC, provides:
This unified approach streamlines the complex process of quantum-safe migration, enabling organizations to protect data across branches, cloud services, and remote users.
FSD Tech specializes in deploying Cato SASE solutions tailored to the unique regulatory and operational needs of UAE and GCC organizations. Services include infrastructure assessments, PQC migration planning, secure tunneling, and compliance-driven upgrade paths. With deep regional expertise, FSD Tech ensures that enterprises can navigate the quantum transition confidently and efficiently.
The first step is to inventory all cryptographic assets across the organization. Identify where encryption is used, which protocols are in place, and which systems are most critical. Automated tools and expert services from providers like FSD Tech can accelerate this process, ensuring comprehensive coverage and minimizing blind spots.
Develop a migration plan that prioritizes high-risk and high-value assets. Align your roadmap with regulatory deadlines and sector-specific frameworks. Engage stakeholders across IT, compliance, and business units to ensure alignment, resource allocation, and executive buy-in.
Deploy PQC solutions such as Cato SASE’s quantum-ready tunnels and enforce identity-based access controls. Establish continuous monitoring to detect new vulnerabilities, track cryptographic health, and ensure ongoing compliance with evolving regulations. Regular reviews and updates are essential as both quantum technology and regulatory requirements evolve.
Facing the 2024 Cryptography Executive Regulation, a major UAE bank partners with FSD Tech to assess its cryptographic landscape. Legacy systems using RSA are identified as high-risk. The bank migrates to PQC-ready tunnels on Cato SASE, implements zero trust access policies, and establishes continuous cryptographic health monitoring. The result: regulatory compliance, enhanced customer trust, and future-proof security.
A Dubai hospital, responsible for safeguarding patient records for decades, adopts Cato SASE and PQC solutions. The migration ensures that sensitive data remains protected against both current and future threats, meeting UAE regulations and international best practices for patient privacy and data integrity.
Book a strategy session with our experts and design your roadmap to quantum safety. Schedule Now
Adversaries are already collecting encrypted data with the intention of decrypting it in the future when quantum computers become powerful enough to break current encryption standards. This means sensitive data stolen today could be exposed years from now, making immediate migration to quantum-resistant cryptography essential for UAE and GCC organizations.
While the exact timeline is debated, most experts and regulatory bodies recommend that organizations begin migrating to post-quantum cryptography by 2028 and complete critical upgrades by 2035. The UAE has accelerated these deadlines for government and critical sectors, reflecting the urgency of the threat.
Organizations should start by inventorying all cryptographic assets, prioritizing critical systems, and developing a migration plan to NIST-approved PQC standards. Engaging with local experts like FSD Tech can streamline this process and ensure compliance with UAE regulations.
Cato SASE, as deployed by FSD Tech in the UAE and GCC, provides unified, PQC-ready network security, identity-based access controls, and continuous cryptographic health monitoring. This enables organizations to manage quantum-safe migration efficiently and maintain compliance with regional mandates.
No. Any organization that stores sensitive or long-lived data—especially in regulated sectors like finance, healthcare, and government—must prepare for quantum threats. The risk is universal, and regulatory requirements in the UAE apply to organizations of all sizes.
Kyber (for encryption) and Dilithium (for digital signatures) are among the first algorithms selected by NIST for standardization. These algorithms are designed to withstand both classical and quantum attacks, providing long-term protection for sensitive data.
The UAE’s Cryptography Executive Regulation is among the most proactive globally, mandating quantum-resistant cryptography for government and critical sectors since 2024. This places UAE organizations ahead of many international peers in terms of compliance and resilience.
Protocols such as TLS, SSH, and IPsec, which rely on RSA or ECC, are particularly vulnerable to quantum attacks. Organizations must assess and upgrade these protocols to quantum-safe alternatives as part of their migration strategy.
FSD Tech offers tailored assessments, PQC migration planning, secure tunneling, and compliance-driven upgrade paths for organizations in the UAE and GCC. Their expertise ensures that enterprises can meet regulatory requirements and achieve quantum resilience efficiently.
STL-QCRYPTO is an industry framework that emphasizes sector-specific migration planning for quantum resilience, particularly in regulated sectors like finance, telecom, utilities, and government. It provides a structured approach to aligning technical migration with compliance and risk management.
Solutions like Cato SASE include cryptographic health monitoring features that provide real-time visibility into the status of cryptographic assets. This allows security teams to detect vulnerabilities, ensure compliance, and respond quickly to emerging threats.
Non-compliance can result in regulatory penalties, increased risk of data breaches, and potential loss of trust from customers and partners. Given the UAE’s strict enforcement, organizations must prioritize compliance to avoid these risks.
Yes. Cato SASE is designed for seamless integration with existing network and security architectures. FSD Tech provides local expertise to ensure smooth deployment and minimal disruption to operations during the migration to quantum-safe security.
Start by identifying assets that store or transmit sensitive or long-lived data, such as financial records, healthcare data, and government communications. Prioritize systems that rely on vulnerable protocols and are subject to regulatory mandates. FSD Tech can assist with comprehensive asset discovery and risk assessment.
Identity-based access enforces zero trust principles, ensuring that only authorized users can access sensitive resources. In the context of quantum-safe security, this reduces the attack surface and complements PQC by controlling who can interact with protected data and systems.
Regularly consult official UAE regulatory authorities, participate in industry forums, and engage with trusted local cybersecurity partners like FSD Tech. Staying informed about regulatory updates and best practices is essential for maintaining compliance and resilience.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts