.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Digital transformation is reshaping the business landscape across Dubai, Abu Dhabi, and the wider Gulf region. Enterprises are accelerating cloud adoption, embracing SaaS platforms, and enabling remote work to drive innovation and agility. However, this rapid evolution brings a hidden challenge: the surge of shadow IT—unsanctioned apps and services used without IT oversight.
Recent studies reveal that 87% of UAE companies have experienced cyber incidents in the past two years, with 13% directly attributed to shadow IT. The risks are particularly acute in sectors like finance, healthcare, and government, where sensitive data and regulatory mandates intersect.
For CISOs, security architects, IT managers, and compliance officers, shadow IT is more than a technical nuisance—it’s a strategic risk. Unmanaged SaaS sprawl undermines visibility, weakens compliance, and exposes organizations to costly breaches. With the average cost of a data breach in the Middle East reaching $8.05 million, proactive shadow IT control is now a board-level priority.
Shadow IT encompasses any application, cloud service, or device used within an organization without explicit IT approval. In the GCC, the phenomenon is widespread and growing, fueled by:
The impact is significant:
These scenarios highlight the daily reality for GCC organizations: productivity gains often come at the expense of security and compliance.
Legacy security tools—such as firewalls, VPNs, and manual audits—were designed for static, on-premises environments. Today’s cloud-first reality renders these approaches inadequate:
Research shows that 65% of SaaS apps in organizations are unsanctioned, and only 12% of IT departments can keep up with new technology requests. This backlog fuels shadow IT, leaving critical vulnerabilities unaddressed.
The financial and reputational stakes are especially high in the GCC:
For regulated sectors such as finance and healthcare, the consequences of unmanaged shadow IT can be catastrophic.
Legacy tools can’t keep pace with SaaS sprawl. Want to know how many shadow apps are hiding in your business? Get a free shadow IT risk snapshot today.
Cato Networks’ SASE platform, delivered in partnership with FSD Tech, provides a unified, real-time approach to shadow IT control. Key components include:
Unlike legacy tools, Cato SASE delivers:
With Cato SASE, IT and security teams can:
Example:
A Dubai-based healthcare provider identifies staff using personal Dropbox accounts for patient data. Cato SASE’s inline CASB flags the activity, blocks risky uploads, and enforces secure, compliant alternatives—protecting both data and regulatory standing.
Cato SASE integrates Zero Trust Network Access (ZTNA) to ensure only authorized users and devices can access sensitive cloud resources. Features include:
Inline DLP and audit logging further enhance security, providing detailed records of who accessed what data, when, and from where—essential for compliance and incident response.
GCC enterprises face a complex regulatory landscape, with mandates such as:
Cato SASE supports compliance by:
Inline Data Loss Prevention (DLP) inspects all traffic for sensitive data—such as financial records, health information, or personal identifiers—and blocks unauthorized uploads or downloads. Audit logging ensures every action is recorded, supporting both internal governance and external regulatory audits.
Use Case:
A healthcare provider in Abu Dhabi can demonstrate to regulators that patient data is never shared via unsanctioned apps, with every access logged and monitored—reducing audit times and regulatory risk.
Struggling to align cloud usage with GCC regulations? Get a tailored shadow IT compliance gap report for your industry.
FSD Tech, as a regional leader in secure cloud adoption, offers shadow IT discovery workshops that combine automated discovery tools with expert analysis. These workshops provide:
FSD Tech configures Cato SASE dashboards to visualize cloud usage, map sanctioned versus risky apps, and define enforcement policies tailored to:
A Dubai-based investment bank was under pressure to enable remote work and digital collaboration. IT discovered analysts using personal cloud storage and messaging apps to share sensitive deal information. FSD Tech deployed Cato SASE, enabling:
Results: Shadow IT incidents dropped by 80%, compliance audit times were halved, and business productivity improved—demonstrating the value of unified shadow IT control.
Shadow IT control is now a strategic imperative, with executive and board-level engagement at an all-time high:
This top-down commitment is crucial for:
Technology alone is not enough. Organizations must foster a culture where security and agility coexist:
Shadow IT is a growing threat for enterprises in the Gulf region, with significant financial, regulatory, and reputational implications. As digital transformation accelerates, the risks of unmanaged cloud usage are only increasing.
Cato SASE, enabled by FSD Tech, delivers a comprehensive solution:
For CISOs, security architects, and IT leaders, the path forward is clear: regain control over your cloud environment, protect sensitive data, and empower your teams to innovate—securely and compliantly.
Ready to regain visibility and secure your SaaS environment? Book a Free strategy session with FSD Tech’s experts and see Cato SASE in action.
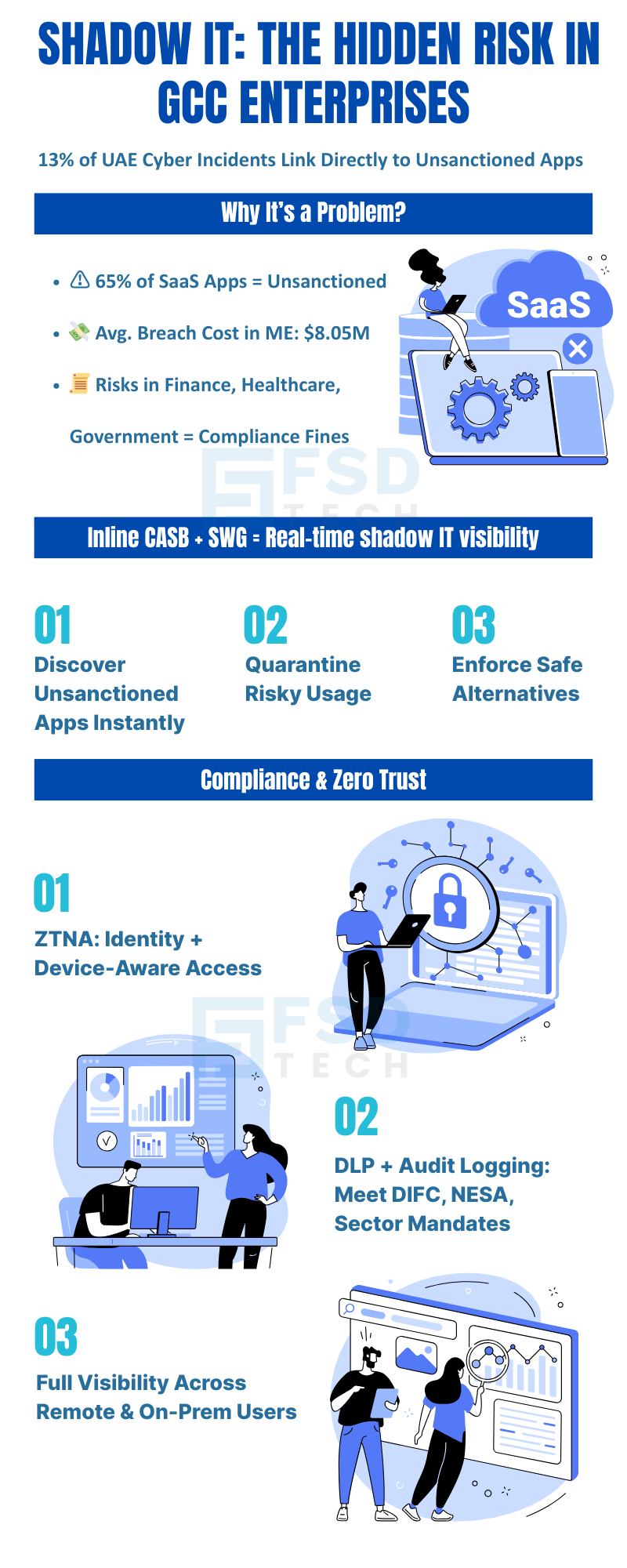
Shadow IT refers to the use of applications, cloud services, or devices outside the control of an organization’s IT department. In the GCC, rapid digitalization and the shift to remote work have made shadow IT a leading cause of cyber incidents, data leaks, and compliance failures. The region’s highly regulated sectors, such as finance and healthcare, are particularly vulnerable due to the sensitivity of the data involved and strict regulatory mandates.
Cato SASE provides real-time discovery of unsanctioned apps through its inline CASB and Secure Web Gateway. It enables IT teams to enforce access policies, quarantine risky services, and integrate Data Loss Prevention (DLP) and audit logging. This unified approach empowers organizations to manage cloud usage without stifling business productivity, ensuring that only approved apps are used across the enterprise.
Key regulations include the DIFC Data Protection Law, NESA standards, and sector-specific mandates for finance and healthcare. These frameworks require robust data governance, auditability, and strict controls over data access, sharing, and retention. Non-compliance can lead to severe penalties and reputational damage.
FSD Tech delivers tailored shadow IT discovery workshops, configures Cato SASE dashboards, and aligns enforcement policies with local compliance requirements. Their expertise ensures that Cato SASE deployments are customized for the unique regulatory and operational needs of GCC enterprises, enabling secure and compliant cloud adoption.
Legacy tools like firewalls, VPNs, and manual audits were designed for static, on-premises environments. They often miss encrypted SaaS traffic, OAuth-authorized apps, and remote access tools that bypass traditional controls. As a result, they provide incomplete visibility and a reactive security posture, leaving organizations exposed to shadow IT risks.
The average cost of a data breach in the Middle East is $8.05 million, nearly double the global average. Shadow IT increases the likelihood of breaches, regulatory penalties, and operational disruption. Proactive control is essential to minimize financial and reputational losses.
Cato SASE integrates Zero Trust Network Access (ZTNA), enforcing identity- and device-aware policies. Access to sensitive cloud apps is granted only to authorized users and compliant devices, with contextual controls based on location, risk level, and user behavior. This approach minimizes the attack surface and supports secure digital agility.
Yes. Cato SASE provides detailed audit logs of all web and app activity, supporting both internal governance and external regulatory audits. Inline DLP ensures that sensitive data is not transferred via unsanctioned channels, helping organizations demonstrate compliance with DIFC, NESA, and other mandates.
An inline CASB (Cloud Access Security Broker) inspects all network traffic in real time, instantly discovering unsanctioned SaaS apps and monitoring usage trends. It enables IT to quarantine risky services, enforce policies, and provide safe alternatives—far surpassing the capabilities of legacy tools.
FSD Tech’s local expertise ensures that Cato SASE deployments are aligned with GCC regulatory frameworks. They map acceptable versus risky SaaS usage, define enforcement policies, and configure dashboards to meet the specific needs of finance, healthcare, retail, and government sectors in the UAE and across the region.
A shadow IT discovery workshop, delivered by FSD Tech, combines automated tools and expert analysis to uncover the true extent of unsanctioned app usage. The outcome is a comprehensive risk assessment, prioritized remediation plan, and stakeholder alignment—laying the foundation for effective shadow IT control.
Cato SASE provides unified visibility and control across all users, devices, and locations—whether on-premises or remote. Its inline CASB and SWG inspect all traffic at the network edge, ensuring that unsanctioned apps are detected and managed regardless of where employees work.
Executive and board-level involvement is critical for effective shadow IT governance. In the GCC, 50% of boards are now engaged in cyber strategy, ensuring that security initiatives have the authority and resources needed to drive organization-wide compliance and risk reduction.
By adopting solutions like Cato SASE and leveraging FSD Tech’s expertise, organizations can enforce robust security controls without hindering innovation. Granular, context-based policies allow legitimate workflows to continue while blocking risky behaviors—supporting secure digital transformation.
Finance, healthcare, government, and retail are particularly vulnerable due to the sensitivity of the data they handle and the complexity of regulatory requirements. These sectors benefit most from unified, real-time shadow IT control and compliance support.
Cato SASE’s inline DLP inspects all traffic for sensitive data—such as financial records or health information—and blocks unauthorized uploads or downloads. This ensures that data is not exfiltrated via unsanctioned apps, supporting both security and compliance mandates in the GCC.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts