.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

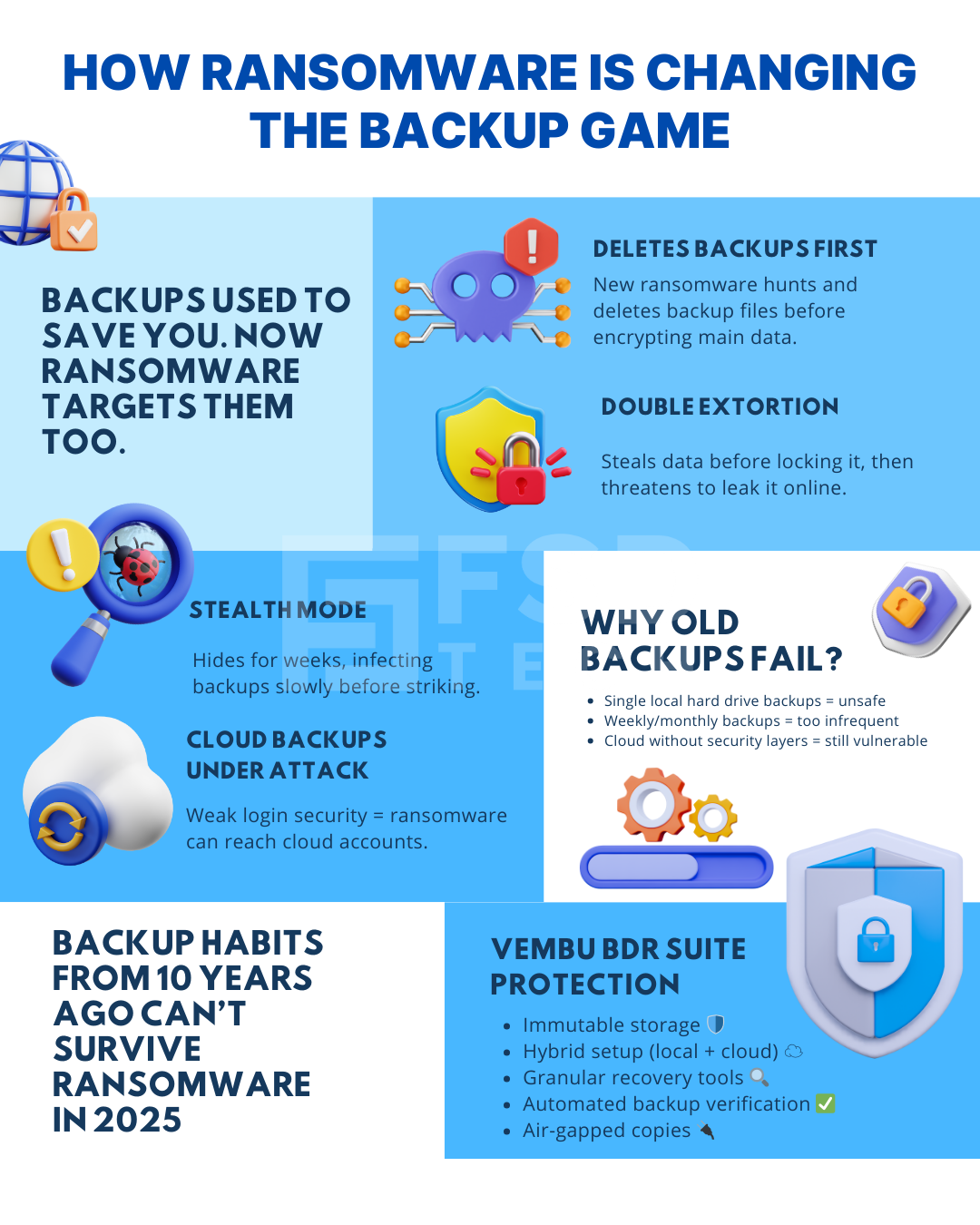
In 2018, ransomware worked like a smash-and-grab robbery — it broke in, encrypted your files, and left you a note asking for money. If you had a recent backup, you could ignore the demand, restore your files, and get back to work.
But by 2025, ransomware has grown up — and it’s nastier than ever.
Today’s ransomware doesn’t just target your files.
It also goes after your backups.
Let’s Start with a Story
Back in 2018, if a hacker attacked your business with ransomware (a type of malicious software), they would lock your files and demand money to unlock them.
If you had a recent backup saved somewhere safe, you could ignore them, restore your files from that backup, and go back to work.
Fast forward to 2025 — the game has changed.
Ransomware has become smarter, more patient, and far more dangerous. Today, hackers know that businesses use backups to recover — so they’ve made it their mission to destroy your backups before you even know you’ve been attacked.
Ransomware is a malicious program that sneaks into your computer systems, locks your files so you can’t use them, and then demands money (a ransom) to unlock them.
It’s like a digital burglar that doesn’t just steal your valuables — it changes the locks on your doors and charges you to get back inside.
1. They Delete Backups Before Locking Files
Older ransomware ignored backups. New ransomware looks for your backup files first and deletes them.
If your backups are gone, you have no safety net.
2. They Steal Your Data Before Locking It (Double Extortion)
Even if you can restore from a backup, hackers now make a copy of your files and threaten to publish them online if you don’t pay.
This is especially bad if you have sensitive customer or financial data.
3. They Stay Hidden for Weeks (Stealth Mode)
Some ransomware doesn’t strike immediately. Instead, it hides inside your systems for days or weeks, slowly infecting your files and even your backups.
When it finally locks everything, you may discover that all your backup copies are already infected.
4. They Go After Cloud Backups Too
Cloud storage used to feel like a safe zone. But modern ransomware can sometimes access your cloud accounts — especially if you use the same password for multiple systems or don’t have extra security steps in place.
Here’s what’s different now:
Many businesses still use backup habits from years ago:
These were fine 10 years ago, but they’re no match for modern ransomware. If attackers can find your backup, they will try to delete, lock, or corrupt it.
Don’t let outdated backups put your business at risk. Claim your free 2025 Data Protection Health Check today. Get Started
To survive today’s ransomware attacks, your backup plan needs to be different. It should include:
1. Immutable Backups
This means your backup files cannot be changed or deleted for a fixed period of time — even by you or your IT admin.
It’s like putting your backup in a vault that automatically locks itself and can’t be opened until the time limit expires.
2. Multiple Backup Locations
Keep at least two copies of your backup:
3. Frequent Backups
The more often you back up, the less data you lose. For important systems, backups every few minutes are possible — not just daily.
4. Backup Encryption
Encrypting backups means scrambling the data so even if hackers steal it, they can’t read it without the encryption key.
5. Regular Backup Testing
A backup you can’t restore is useless. Test your backups regularly to make sure they actually work — and that you have clean copies from before an infection began.
Vembu BDR Suite is designed for the realities of 2025:
Real-Life Example
A construction company in Oman was hit by ransomware that deleted their on-site backups.
But because they used Vembu’s immutable cloud backups, they restored all their project files from a clean copy taken 10 days earlier — without paying a single dirham in ransom.
The Big Lesson
Ransomware today is not just about locking your files — it’s about taking away your ability to recover.
The old saying “just back it up” isn’t enough anymore. You need a ransomware-proof backup plan to protect your business.
Tomorrow’s Topic – We’ll explore “Immutable Backups: What They Are and Why You Need Them” in detail.
If your current backups aren’t built for ransomware in 2025, you’re leaving the door wide open.
Let’s run a free ransomware readiness check for your business. Book now
1. What exactly is ransomware?
Ransomware is a type of harmful computer program that sneaks into your systems, locks your files so you can’t open them, and then demands money to unlock them.
Think of it like someone breaking into your office, locking your filing cabinets with a new padlock, and then asking you to pay to get the key — except it’s all done digitally, and it can happen in seconds.
2. Why is ransomware more dangerous now than before?
In the past, ransomware would simply lock your files and wait for you to pay. If you had a recent backup stored safely, you could restore everything without paying.
Now, ransomware has gotten much smarter:
3. What is “double extortion” in ransomware?
This is a two-part threat:
4. Can ransomware really attack my cloud backups?
Yes, if your cloud backups are linked to your main network or if they use the same passwords. Some ransomware strains can log into your cloud account and delete or encrypt backups there.
That’s why your cloud backups need extra protection — such as separate login credentials and special settings to make them “undeletable” for a period of time.
5. How does ransomware delete backups?
If your backup is stored on the same network, server, or connected drive as your main files, ransomware can access it just like it accesses your regular data. Once inside, it can delete or damage those backups so you have nothing to restore from.
6. What is an immutable backup and why is it important?
An immutable backup is a backup that cannot be changed, edited, or deleted for a set period of time — not even by someone with administrator access.
It’s like locking your backup in a time-locked safe. You can only open it after a set number of days, and until then, nothing can be altered inside it. This means ransomware can’t touch it.
7. Why do I need backups in more than one place?
Keeping backups in multiple locations ensures you have a plan B if something goes wrong:
8. How often should I back up my data to protect against ransomware?
The more often you back up, the less you lose.
For highly important data, backups can be done every few minutes. For general business data, at least once a day is recommended.
Ask yourself: “If my systems went down now, how much work could I afford to lose?” That answer will guide your backup frequency.
9. What does “backup encryption” mean?
Backup encryption means scrambling your backup files so that no one can read them without a special key.
Even if hackers steal your backups, encrypted backups are useless to them because they can’t open or understand the data.
10. What does “air-gapped backup” mean?
An air-gapped backup is a copy of your data that is stored completely separate from your main systems — it’s not connected to your network most of the time.
This could be a physical device kept offline or a cloud system that ransomware can’t access directly. Think of it as a copy of your data locked in a completely separate building.
11. How does Vembu BDR Suite protect against modern ransomware?
Vembu uses several layers of protection:
12. Is testing my backups really necessary if they run automatically?
Yes. Even automated backups can fail due to corrupted files, misconfigurations, or storage issues. Regular testing ensures:
13. If I pay the ransom, will I definitely get my files back?
No. Many companies pay and still never get their data back. Some hackers disappear after payment; others send corrupted files. Paying also marks you as a target for future attacks.
14. How can I check if my backups are ransomware-proof?
Ask yourself:
15. What’s the first step I should take to improve my ransomware protection?
Have a ransomware readiness check done by a trusted provider like Vembu. This will review your current backup system, identify weaknesses, and give you a step-by-step plan to fix them.
Want tailored advice for your business? Schedule a Free Consultation with Our Experts Now. Schedule a Call

Nasmal is a Solution Architect & Business Analyst focused on AI, Data, Automation, BCP, and Process Optimization. He helps businesses evolve from reactive to proactive, data-driven, and resilient operations. With hands-on expertise, he simplifies complex tech into clear, easy-to-understand blogs.
Share it with friends!

🕓 November 24, 2025

🕓 September 16, 2025

🕓 September 5, 2025
share your thoughts